When most people think about the internet, they picture Google, social media, and the websites we visit every day. But beneath the surface web lies a different are, the dark web, and at its center sits one of its most well-known topics: The Hidden Wiki.
How to Access The Hidden Wiki Safely (For Research/Education Only)
Step 1: Use a Paid VPN First
Step 2: Download and Install Tor Browser
- Go to the official Tor Project website: https://www.torproject.org.
- Download the Tor Browser for your operating system.
- Verify the download signature.
- Install it like any other application.
- Do NOT install any plugins or extensions.
Step 3: Configure for Maximum Security
- Open Tor Browser (with VPN connected).
- Click the shield icon, then select the “Standard” security level.
- Never maximize the browser window.
- Do NOT log into personal accounts.
Step 4: Access The Hidden Wiki
- Type a .onion address in the address bar.
- Note: The Hidden Wiki addresses change frequently, so you’ll need to find current ones through security forums or threat intelligence sources.
- Be patient, sites load much more slowly.
- Never click on links you don’t trust.
- Never download files unless absolutely necessary.
Examples of Legitimate .onion Sites
Hidden Search Engines
- OnionIndex Search Engine – OnionIndex Search Engine
- DuckDuckGo – DuckDuckGo Search Engine
- OnionLand – OnionLand Search
- tordex – tordex
- Torch – Torch
- Ahmia – Ahmia
- MetaGer – MetaGer – German Search
- haystak – haystak
Store Links
- Tor Shop – Tor Shop – Multi Vendor Marketplace | Build-in Escrow
- BlackMart – BlackMart
- Caribbean Cards – Caribbean Cards
- Psy Shop – Psy Shop – Drugs Market
- Cardzilla – Cardzilla
- 21 Million Club – 21 Million Club
- Bidencash – Bidencash
- Horizon Store – Horizon Store
- The Escrow – The Escrow
- Black Market Reloaded – Black Market Reloaded – offline
- Abraxas – Abraxas – offline
- AlphaBay – AlphaBay – offline
Email Providers
- ProtonMail – ProtonMail
- Alt Address – Alt Address
- secMail – secMail
- TorBox – TorBox
- Elude.in – Elude.in
- adunanza OnionMail Server – adunanza OnionMail Server
- tempmail + – tempmail +
- Onion Mail – Onion Mail
- DNMX – DNMX
- Mail2Tor – Mail2Tor
- Cockmail – Cockmail
- Confidant Mail – Confidant Mail
- Underwood’s Mail – Underwood’s Mail
Forums / Social / Chat
- dread – dread
- Deutschland im Deep Web Forum – Deutschland im Deep Web Forum
- Hidden Answers – Hidden Answers
- SuprBay – SuprBay: The PirateBay Forum
- Rutor – Rutor
- Lolita City – Lolita City
- Endchan – Endchan
- Raddle – Raddle
- MadIRC – MadIRC
- The Stock Insiders – The Stock Insiders
- Facebook – Facebook
- Ableonion – Ableonion
- Adamant – Adamant Decentralized messenger
- ~/XSS.is – XSS.is – Russian Hacking Forum
- HackTown – HackTown
- NZ Darknet Forum – NZ Darknet Market Forums
- The Calyx Institute (Jabber) – The Calyx Institute (Jabber)
- AN0NYM0US’z F0RUM – AN0NYM0US’z F0RUM
Onion Hosting / Domain Services / File Sharing
- Freedom Hosting Reloaded – Freedom Hosting Reloaded
- SporeStack – SporeStack
- Ablative Hosting – Ablative Hosting
- BlackCloud – BlackCloud
- ZeroBin – ZeroBin
- Keybase – Keybase
- SecureDrop – SecureDrop
- OnionShare – OnionShare
- NJALLA – OnionShare
- Ablative.Hosting – Ablative.Hosting
- OnionLand Hosting – OnionLand Hosting
- PRIVEX – PRIVEX Hosting
- Kowloon Hosting – Kowloon Hosting
- TorPress – TorPress, Free wordpress hosting
- Kaizushi – Kaizushi PHP, Django and Rails hosting and VPS
- OnionName – OnionName
- Garlic – Onion Generator – Garlic – Onion Generator
- TorShops – TorShops
VPN
- Mullvad VPN – Mullvad VPN
- cryptostorm – cryptostorm
- AirVPN – AirVPN
Whistleblowing / News
- ProPublica – ProPublica
- The Guardian – The Guardian | SecureDrop
- AfriLEAKS – AfriLEAKS
- The Intercept – The Intercept
- The CIA – CIA
- FLASHLIGHT – FLASHLIGHT
- VOA – VOA
- New York Times – The New York Times
- BBC – BBC
- bellingcat – bellingcat
- The Tor Times – The Tor Times
- RadioFreeEurope RadioLiberty – RadioFreeEurope RadioLiberty
- Organized Crime and Corruption Reporting Project – Organized Crime and Corruption Reporting Project
- Joker.buzz – Joker.buzz
- Privacy International – Privacy International
- DW News – DW News
- BalkanLeaks – BalkanLeaks
- BuzzFeed News – BuzzFeed News
Non English Websites
- Cebulka – Cebulka – Polish Onion Forum
- DimensionX – DimensionX – Another Polish Forum
- XMundo – XMundo – Turkish Dark Web Forum
- Germania – Germania – German Dark Web Forum
- Bibliothèque – Bibliothèque – French Darknet book library
Others
- RelateList – RelateList
- Hacker Game – Hacker Game
- Tech Learning Collective – Tech Learning Collective
- cryptostorm – cryptostorm
- PsychonauticsWIKI – PsychonauticsWIKI
- AgoraDesk – AgoraDesk
- Njalla – Njalla
- LocalMonero – LocalMonero
- The CIA – The CIA
- NCIDE Task Force – NCIDE Task Force
- National Police of the Netherlands – National Police of the Netherlands
- Fake ID Generator – Fake ID Generator
- Check your anonymity online – Check your anonymity online
- Beneath VT – Beneath VT
- Go Beyond – Go Beyond
- Deep Web Radio – Deep Web Radio
- DNM Bible – DNM Bible
- xmrguide – xmrguide
- JUST ANOTHER LIBRARY – JUST ANOTHER LIBRARY
- Bible4u – Go Beyond
- Zlibrary – Zlibrary
- Comic Book Library – Comic Book Library
- The Secret Story Archive – The Secret Story Archive
- Tor Project – Tor Project
- riseup – riseup
- Debain OS – Debain OS
- Russian Books – Russian Books
- Russian Torrent / Forum – Russian Torrent / Forum
- Sonic & Tails – Sonic & Tails
- phdcasino – phdcasino
- Webpage archive – Webpage archive
- OpenPGP Keyserver – OpenPGP Keyserver
- coinpayments – coinpayments
- Tor Metrics – Tor Metrics
- DEEPDOTWEB – DEEPDOTWEB
- superkuh – superkuh
- Connect – Connect
- We Fight Censorship – We Fight Censorship
- IIT Underground – IIT Underground
- Clockwise Library – Clockwise Library
Warning About Scam Links
- deepmk42fqasmnr2njaoo2pd5og5pdw7j3pmotrm7ohjgrbzmfdk6sid.onion
- hiddenn5vz32vqp3tu4djjzejyajcri4uxqpukf643plp72m2g4hsiad.onion
- deepma5ecekx4nqaepjei3iznumjvnsxp4wpxbiusa23tmflma7o4tqd.onion
- walmart2s6jjopnmynagwm7i4fgosmkitrhd4b7nbqaxglfbjm6sguid.onion
- torzon4kv5swfazrziqvel2imhxcckc4otcvopiv5lnxzpqu4v4m5iyd.onion
- imperiagyuyeusw5lg6koiltvawuu4qukqnn5rrsn3uvedlk722w6lad.onion
- torbay5fazkp7mkihetyfafc5d3aa3j6rd62irtcxozscffb2gzzbeqd.onion
- torbuyit4x2zvwiscqk5cujv7nqbkxokj73beekolo5mmugodseppjqd.onion
- deepma33mz5ndfcszwz65nteyzxe2pcpjq5tkiattrvi3u62egmldoyd.onion
- courierr3ooode7zdopy2q7lvsyxev7owywz5cn4tx62fiucyrgnneyd.onion
- ly75dbzixy7hlp663j32xo4dtoiikm6bxb53jvivqkpo6jwppptx3sad.onion
- deepmarn4jdhginkt2srb77hgktyomdrmmdeyxlmvdixr4dxn4mlszid.onion
- deepmancalrrxivpsbsrqz7etgu24neishqj7bnzq7c3cpzjeqcld5id.onion
- protectb3xjr5nfbj4m435ymbsti3uw7wtimux4232zgqzu3ohpqewyd.onion
- shadowm4vpk2xffxqx5ngu5ckrq63oraoyb6hs7w23ypzckmgnqyeaad.onion
The links above originate from the official dark web scam list. Check their discussion for more details.
Important Reminders
- Keep your VPN connected the entire time.
- Never enter personal information.
- Use a separate device if possible.
- Assume everything could be a trap.
- Don’t access for curiosity’s sake alone.
Support the Tor Project
What Is The Hidden Wiki?
The Hidden Wiki is basically a directory of dark web sites, similar to how Yahoo! once worked as a directory for the early internet. However, instead of regular websites, it lists .onion addresses—sites accessible only through the Tor browser. Think of it as a phonebook for the anonymous internet, except that it contains entries ranging from privacy tools to criminal marketplaces.
The site has been around since the early 2010s, going through many versions as law enforcement shuts down copies and new ones appear in their place. It’s not a single site but rather an idea that’s been copied many times across different servers. What makes The Hidden Wiki different from regular directories is its lack of central authority. Anyone can create a version, and the content ranges widely in legality and ethics.
The Hidden Wiki History and How It Changed
The Silk Road marketplace, launched in 2011, became a famous example for dark web commerce, and The Hidden Wiki became one of the main ways users found it. When the FBI shut down Silk Road in 2013 and arrested its founder, Ross Ulbricht, it marked a turning point. The takedown showed that Tor wasn’t as bulletproof as many believed, using a combination of server vulnerabilities, traffic analysis, and traditional detective work.
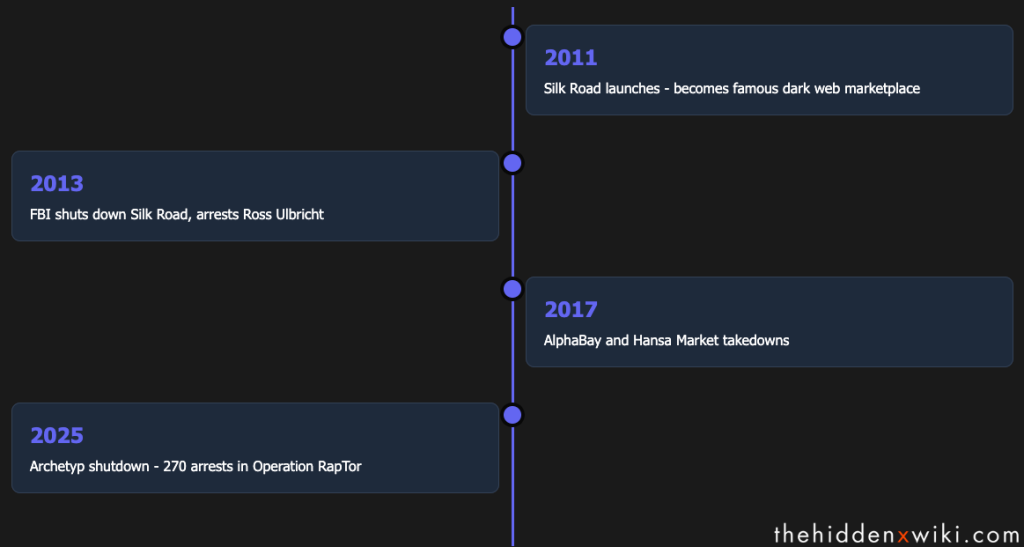
Since then, The Hidden Wiki has been constantly changing. Versions have been hacked, taken over by different groups, and shut down by authorities. Some versions are suspected of being honeypots—sites run by law enforcement to monitor visitors and collect information.
What You’ll Find on The Hidden Wiki
Legitimate Services
- Secure email providers like ProtonMail’s Tor version
- Encrypted messaging platforms for activists and journalists
- Anonymous forums for people in harsh regimes
- Whistleblowing platforms similar to SecureDrop
- Privacy-focused search engines
- Cryptocurrency services
Illegal Content
- Marketplaces for drugs, weapons, and stolen data
- Hacking services and malware
- Stolen credit card information and identity documents
- Counterfeit currency and documents
- Forums for discussing illegal activities
The Hidden Wiki and Recent Developments in 2025
Major Takedowns
Cryptocurrency Tracking
Modern Ransomware
Hidden Wiki Security Lessons for Professionals
Threat Intelligence
Employee Education
Incident Response
A Word of Caution

